The work process
This is the process we use to protect and secure your intangible assets. With this method of turning your idea, vision, data etc. into an asset, we go through four steps. We identify them, manage them and monitor them throughout their lifecycle. And when needed, we help you enforce your rights. So each step has a specific and important task in securing your intellectual property.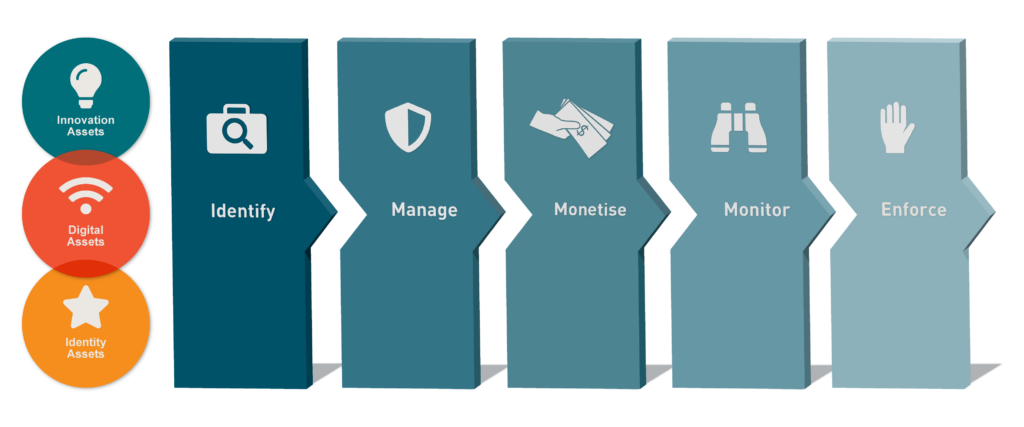
Same process, different tools
The steps and the process are all the same but depends on which area of asset we are handling; we use different tools and services to get the job done. Below you can read more about the four steps of our process.Identify
Identify
Our first step always is to understand your business and industry in order to identify your core business assets: Do you have the right assets? How can we develop your assets? What are your business identifiers? How do your clients perceive you? By locating your strongest assets, we make room for you to develop your core business and increase its value.Manage
Manage
In this step, we consolidate all your assets and implement the best strategy for how to protect them. We can help you protect your data and software, register domain names and trademarks, draft & file patent applications and ensure that your assets are renewed in time. We can also handle your cyber security issues or many other tasks relative to your IP.Monetise
Monetise
Monetisation can take many forms. Extracting value from your assets can mean identifying new or unrealised revenuestreams, but it also means supporting growth, protecting market share and funding further innovation. We can help you
to explore commercial viability and opportunities through licensing, transactions, brand enhancement and protecting
what makes your organisation unique.
Monitor
Monitor
Once we have protected and secured your assets, we can monitor them in order to keep track of how they are used and exposed. We can also monitor the market, global trends and your competitors’ activities to help you stay up-to-date on developments in your industry and prevent any unauthorised use of your assets.Enforce
Enforce
It may be necessary to take legal action in order to protect your intellectual property rights and maintain the value of your intangible assets. If you need to defend or enforce your rights, we can represent you in court or provide you with litigation support. We can also investigate criminal behaviour online, such as data theft, phishing attacks or extortion.